Last Updated on February 3, 2026 by DarkNet
In 2026, VPNs and Tor solve different problems for lawful privacy, censorship resistance, and sensitive research. This guide compares trust, performance, and risk so you can choose deliberately.
What Changed in 2026: Surveillance, Censorship, and the VPN/Tor Landscape
Network privacy tools evolve alongside surveillance, advertising, and bot defense. In 2026, both VPNs and Tor remain valuable but face sharper tradeoffs. Deep packet inspection has improved, bot defenses are more aggressive, and platform trust requirements are tighter. The right choice depends on your adversaries and your tolerance for friction.
Trends in DPI, SNI/ESNI, and traffic correlation capabilities
Modern DPI focuses less on content and more on metadata, timing, and TLS fingerprinting. TLS 1.3 hides more handshakes, and Encrypted Client Hello aims to protect server names, but adoption is uneven. Expect more correlation attempts across traffic timing, destination clusters, and account logins. For background, see IETF TLS 1.3 RFC 8446 and ECH work in IETF draft documents.
Tor network health: relays, bridges, and censorship resistance
Tor relay counts and bridge availability fluctuate as censors and defenders iterate. Pluggable transports like obfs4 and meek continue to help in blocked regions. Monitor network health on Tor Metrics and use bridges when ISPs or states throttle or block public Tor. See Tor Metrics and bridge guidance in the Tor Browser Manual here.
VPN market shifts: consolidation, audits, and law enforcement pressures
VPN consolidation continues, increasing correlated risk from shared infrastructure and ownership. Independent audits and transparency reports matter more than marketing. WireGuard-based services and self-hosted options are common. Authorities increasingly target endpoints and providers, not just traffic. Favor providers with repeat audits, clear disclosures, and simple, open clients.
Core Differences: How VPNs and Tor Route Traffic and What That Means for Anonymity
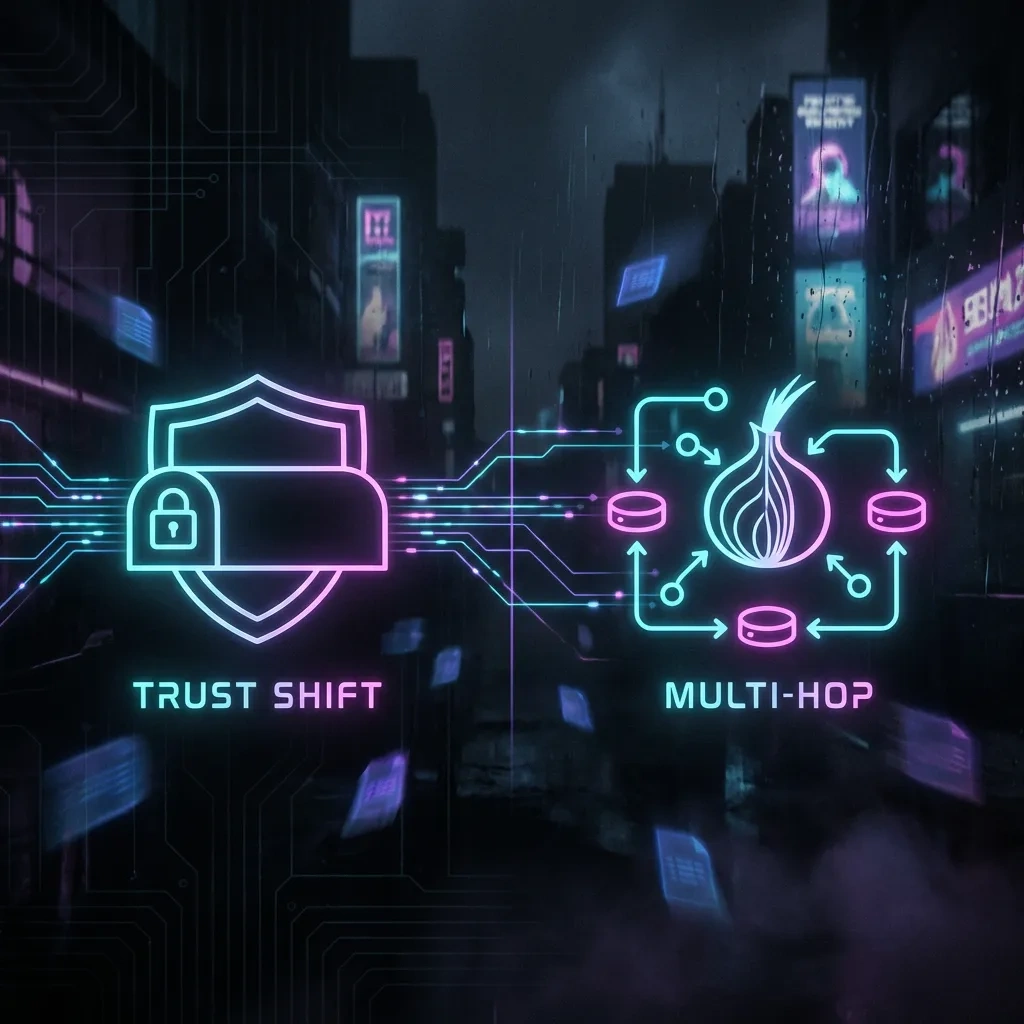
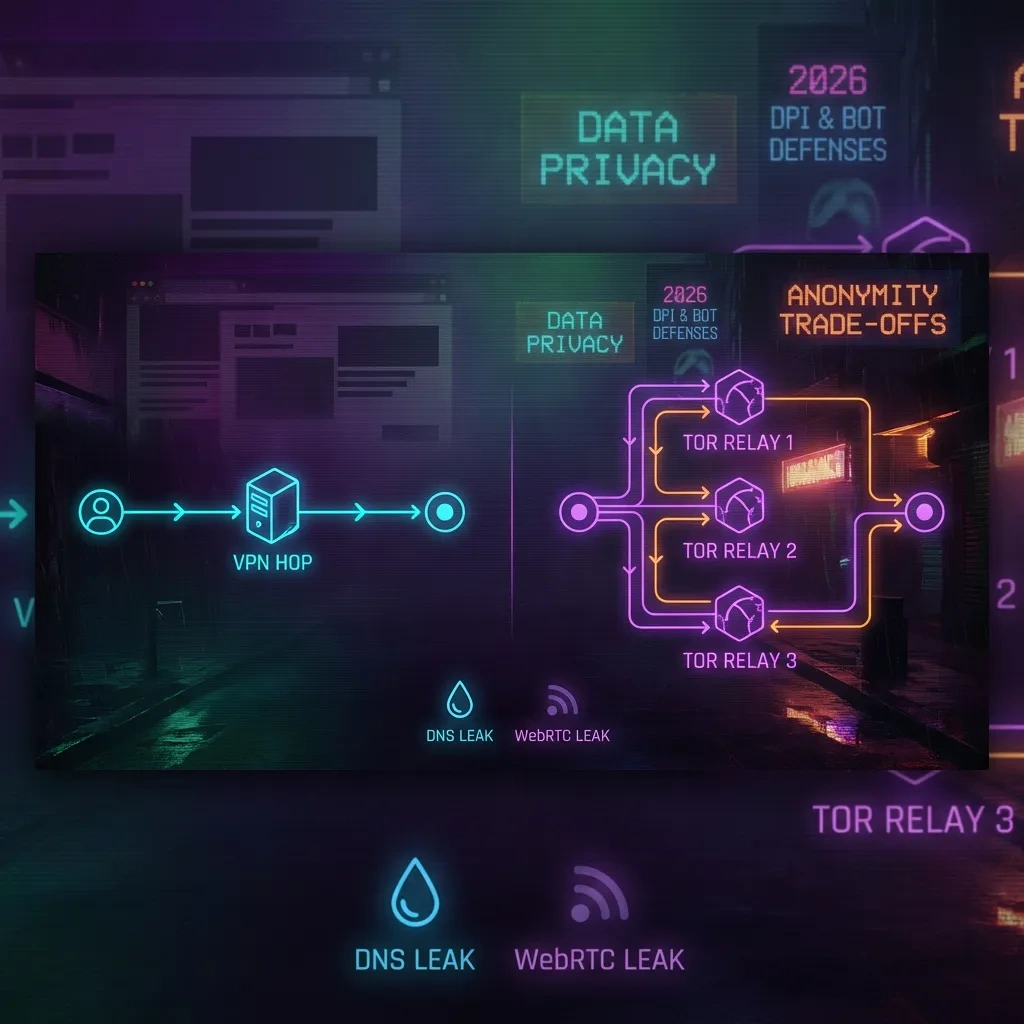
VPNs and Tor solve different problems. VPNs create a single encrypted tunnel to a provider you choose. Tor uses layered encryption across multiple volunteer relays. These architectures lead to different trust assumptions, visibility, and failure modes.
Single hop trust (VPN) vs multi-hop relay trust (Tor)
A VPN centralizes trust in one provider that sees your real IP and destination metadata. Tor distributes trust across entry, middle, and exit relays, so no single relay should see both your identity and your destination under normal conditions.
What each party can see: ISP, VPN, Tor entry/exit, destination
- ISP: With a VPN, your ISP sees you connecting to a VPN and nothing beyond. With Tor, your ISP sees Tor usage unless you use bridges.
- VPN: Sees your real IP and the sites you connect to in metadata terms, but not content if end-to-end HTTPS is used.
- Tor entry: Sees your real IP but not your destination. Tor exit: Sees the destination, and potentially plaintext if you use non-HTTPS.
- Destination site: Sees the VPN egress IP or Tor exit IP, plus browser fingerprint and account identifiers.
Identity vs location privacy vs content confidentiality
- Identity privacy: Tor generally offers stronger network-level anonymity for browsing when used with Tor Browser.
- Location privacy: Both can hide your IP from sites. VPNs are simpler for consistent region selection.
- Content confidentiality: Both rely on TLS to protect content end to end. The tunnel only protects hops between you and the first hop.
VPN vs Tor comparison table
| Dimension | VPN | Tor |
|---|---|---|
| Anonymity | Trust shift to provider. Strong pseudonymity if you control accounts and fingerprints. | Multi-hop anonymity for web browsing with Tor Browser. Stronger against single-entity observers. |
| Trust assumptions | Provider integrity and policies are critical. | Diversity of relays and guard safety are critical. |
| Metadata visibility | Provider sees your IP and destination metadata. | Entry sees your IP, exit sees destination. No single Tor relay should see both. |
| Performance | Usually fast. Good for streaming, calls, gaming. | Slower due to multi-hop routing. Not ideal for high bandwidth use. |
| Blocking and captchas | Moderate. Some IP ranges flagged, but less friction than Tor. | High. Many sites challenge or block Tor exits. |
| Ease of use | Simple apps and kill switches. OS-wide tunnel. | Tor Browser is easy for web. System-wide Tor needs care. |
| Failure modes | Provider logging, DNS leaks, split tunnel mistakes. | Exit node observation, misusing non-Tor apps, deanonymizing behavior. |
Threat Models That Matter: ISP Logging, VPN Provider Risk, Exit Nodes, and Endpoint Exposure
Threat model primer: Define who might observe you and what they can compel. Common adversaries include your ISP or workplace network, a VPN provider, hostile Tor exits, destination websites and ad networks, and in some countries state-level censors. Goals vary: content confidentiality, location privacy, identity anonymity, and censorship resistance. Tools like VPNs and Tor protect network paths, but devices and accounts often reveal more than traffic.
ISP adversary and local network attackers (Wi-fi, workplace)
A VPN or Tor prevents local observers from reading your traffic contents when TLS is used and hides specific destinations from the local network. In restrictive environments, Tor bridges or obfuscated VPN transports may be needed to avoid blocks. See EFF’s privacy primers here.
VPN provider compromise, subpoenas, and logging realities
No-logs claims require evidence. Prefer providers with multiple independent audits and clear, simple architecture. Even then, legal orders can compel real-time measures. A VPN is not anonymity in itself. It is a trust transfer.
Tor exit node observation and HTTPS limitations
Tor exits can observe destination and any plaintext. HTTPS prevents exits from reading page contents, but exits still see domains and timing. Avoid plaintext protocols over Tor. Read Tor’s guidance on exits and HTTPS here.
Endpoint risks: malware, browser exploits, and account logins
Device compromise defeats network privacy. Browser fingerprinting and account logins tie activity to identities regardless of IP. Keep systems updated, minimize risky extensions, and avoid mixing personal and sensitive accounts.
Performance and Reliability in 2026: Latency, Blocks, Captchas, and Streaming vs Browsing
Performance is often the deciding factor. Tor’s multi-hop design trades speed for anonymity. VPNs trade centralized trust for lower latency and fewer captchas.
Latency expectations and bandwidth constraints for Tor circuits
Tor relays vary in capacity. Expect higher latency and lower throughput than a good VPN. Long downloads, large syncs, or real-time calls are unreliable on standard Tor circuits. Tor Browser intentionally standardizes behavior for privacy, which also affects performance.
VPN speed variability: peering, congestion, and protocol choice
VPN speeds depend on provider peering, congestion, nearest egress, and protocol. WireGuard often outperforms other protocols due to streamlined cryptography. See WireGuard. OpenVPN remains versatile but heavier docs.
Website blocks, bot defenses, and why Tor triggers friction
Tor exit IPs are widely flagged, producing captchas and blocks. Some VPN ranges also trigger bot defenses, but the friction is often lower. Browsing with Tor works best for text-heavy sites and research, less so for interactive platforms.
When reliability matters: long sessions, downloads, and VoIP
For long sessions and steady throughput, a reputable VPN is usually better. Tor is best kept for specific browsing sessions that benefit from stronger network anonymity.

Configuration and OpSec Basics (Defensive Use): DNS, WebRTC, Fingerprinting, and Updates
Technical posture and habits often matter more than which tunnel you pick. Keep recommendations high level and lawful. Avoid risky tweaks that break isolation.
Avoiding leaks: DNS, IPv6, WebRTC, and kill switches
- DNS: Ensure DNS queries flow through the tunnel or resolver you intend. Understand DoH tradeoffs RFC 8484.
- IPv6: Use providers that support IPv6 or disable it at the tunnel if not supported to avoid leaks.
- WebRTC: Can reveal local and public IPs in browsers. Review vendor guidance, for example Mozilla’s notes here.
- Kill switch: Prevents traffic from escaping if the tunnel drops.
Browser fingerprinting: why private mode is not anonymity
Private mode clears history but does not standardize your fingerprint. Tor Browser deliberately resists fingerprinting at cost to convenience. See Tor Browser Manual overview.
Safer browsing habits: updates, isolation, and minimizing plugins
- Updates: Apply OS and browser patches promptly. See OS vendor security portals such as Microsoft Windows servicing overview and Android security bulletins here.
- Isolation: Separate sensitive sessions from personal logins. Consider different browsers or profiles.
- Extensions: Fewer is safer. Each plugin increases fingerprint uniqueness and attack surface.
Account hygiene: separating identities and avoiding cross-login
Network tools do not fix account linkages. Using the same email, phone number, or social logins across personas will correlate them regardless of your IP.
VPN over Tor vs Tor over VPN: When Each Layering Pattern Helps (and When It Hurts)
Layering can help in specific cases, but it often adds complexity and new risks. If you are not sure you need a chain, keep it simple.
VPN over Tor: protecting against exit node observation vs added attack surface
VPN over Tor means you connect to Tor first, then start a VPN inside Tor. This can shield Tor exits from seeing your destination and can help reach sites that block Tor exits. Downsides include account or payment risk with the VPN provider, potential deanonymization if the VPN app leaks outside Tor, and more moving parts to misconfigure.
Tor over VPN: hiding Tor usage from ISP vs shifting trust to the VPN
Tor over VPN means you start a VPN, then use Tor through it. This can hide Tor usage from an ISP that blocks it. The VPN still sees that you connected to Tor and could throttle or log. You also become reliant on the VPN’s leak protections.
Bridges, pluggable transports, and when they beat VPN layering
In many censored environments, Tor bridges and pluggable transports are simpler and safer than layering with a VPN. See Tor’s bridge options here.
Misconfigurations that de-anonymize: split tunneling and proxy misuse
Split tunneling can leak traffic. Proxying non-browser apps through Tor without isolation can expose identity. If you must chain tools, test for leaks and keep the design minimal.
Use-Case Matrix: Research, Journalism, Whistleblowing, Geo-Restrictions, and High-Risk Environments
Pick the tool for the job. The matrix below reflects typical tradeoffs under lawful use.
| Scenario | Tool | Why |
|---|---|---|
| Low-risk privacy on travel Wi-fi | VPN | Encrypts local link, stable performance, fewer captchas. |
| Tracking reduction during general browsing | Both | VPN hides IP from sites, Tor Browser resists fingerprinting. Choose based on friction tolerance. |
| Censorship circumvention where Tor is blocked | Tor with bridges | Bridges and pluggable transports are designed for this use case. |
| Censorship circumvention where VPNs are blocked | Tor with pluggable transports | DPI evasion built into Tor’s transport ecosystem. |
| Sensitive research and source protection | Tor | Stronger network anonymity for web activity when paired with Tor Browser. |
| Geo-restricted streaming | VPN | Stable region selection and throughput. Tor is not suitable for streaming. |
| VoIP or real-time collaboration | VPN | Lower latency and fewer blocks. |
| High-risk environments with selective blocks | Bridges or obfuscated VPN | Pick the transport that passes local DPI without raising flags. Keep it lawful. |
| Access to sensitive accounts you want to keep linked to your identity | Neither | Use your normal connection or corporate VPN to avoid triggering risk systems or violating policy. |
Provider and Tool Selection Criteria: Audits, Jurisdictions, Payment Options, and Open-Source Clients
For VPNs, choose boring over flashy. For Tor, use official software and learn the basics.
No-logs claims vs independently verified audits and transparency reports
Look for repeat third-party audits, public methodologies, and simple infrastructure that reduces data collection. Treat warrant canaries cautiously. For context, see EFF’s canary FAQ here.
Jurisdiction and corporate structure: what can be compelled
In some jurisdictions, providers can be compelled to log or assist. Multi-entity structures complicate this but can also obscure accountability. Read transparency reports and legal process summaries carefully.
Protocol and client considerations: WireGuard/OpenVPN, open-source apps
Favor providers with well-reviewed, open-source clients and modern protocols. WireGuard for performance and simplicity. OpenVPN for compatibility. Avoid proprietary tweaks that hinder audits.
Payments and privacy: tradeoffs without enabling wrongdoing
Payment methods can reveal identity. If you require privacy, consider methods that reduce exposure while staying legal and compliant with provider terms. Do not use tools or payments to facilitate wrongdoing.
Common Myths and Failure Modes: I’m Anonymous Assumptions, Leaks, and Human Error
Myth: VPN equals anonymity; reality: it is a trust shift
A VPN can improve privacy from your ISP and local networks, but the provider becomes a new observer. Pick carefully and manage expectations.
Myth: Tor is magic; reality: endpoints and behavior matter
Tor helps at the network layer, but your device, accounts, and content can still reveal identity. Stick to Tor Browser for browsing and avoid adding plugins.
Operational mistakes: reusing emails, phone numbers, and handles
Reusing identifiers links personas across sessions and tools. Separate identities fully if you need separation.
Device compromise beats network privacy tools every time
Malware, keyloggers, and browser exploits bypass tunnels. Maintain updates, backups, and least-privilege settings.
Practical Recommendations and a 2026 Decision Checklist
You do not need every feature. Choose what fits your risk and constraints.
Choosing based on your adversary and acceptable trust assumptions
- If your main adversary is your ISP or hotel Wi-fi: a reputable VPN is often sufficient.
- If your goal is stronger browsing anonymity: use Tor Browser and accept performance tradeoffs.
- If your ISP blocks Tor and you must browse anonymously: try Tor bridges or, if legal, Tor over VPN with a trusted provider.
- If performance and region control are key: choose a VPN with strong peering and simple, audited clients.
Minimum viable setup for privacy-conscious users
- Keep OS and browsers fully updated.
- Use a reputable VPN for everyday link protection and basic tracking reduction.
- Use Tor Browser for sensitive browsing sessions, not general streaming or large downloads.
- Avoid mixing identities and minimize extensions.
Red flags checklist: free VPNs, sketchy extensions, and risky tweaks
- Free or ad-supported VPNs that monetize traffic or inject code.
- Browser extensions promising anonymity without clear documentation.
- Split tunneling defaults that leak DNS or traffic.
- Disabling security features to speed things up.
When to seek legal guidance or professional security support
If your work involves sensitive sources, regulated data, or jurisdictional risk, consult legal counsel and professional security teams. Privacy tools are part of a broader program, not a complete solution.
A 2026 decision checklist
- Define adversaries and goals: confidentiality, location privacy, censorship resistance, or anonymity.
- Decide acceptable trust: single provider trust vs distributed relay trust.
- Pick performance tier: high throughput needs favor VPNs.
- Plan for blocks: Tor bridges or obfuscated VPN if lawful in your region.
- Harden endpoints: updates, minimal plugins, WebRTC controls, DNS handling.
- Test for leaks: IP, DNS, and IPv6 behavior with and without the tunnel.
- Operational discipline: separate accounts and sessions for distinct roles.
- Review provider transparency: audits, open-source clients, and legal process policies.
FAQ
Is Tor safer than a VPN for anonymity in 2026?
For web browsing anonymity, Tor with Tor Browser generally offers stronger network-level anonymity because no single relay should see both your identity and destination. A VPN can provide privacy from your ISP and websites but centralizes trust in one provider. Endpoints and behavior still matter in both cases.
Can my ISP see that I’m using Tor or a VPN?
ISPs typically recognize VPN and Tor traffic patterns. Bridges and pluggable transports can make Tor less visible. Some VPNs use obfuscation to look like regular HTTPS. Visibility varies by DPI capability and local policy.
What are the main risks of Tor exit nodes, and how does HTTPS change that?
Exits can observe destinations and any plaintext. HTTPS protects page contents from exits. Still, exits see domains and timing. Avoid non-HTTPS protocols over Tor whenever possible. See Tor’s HTTPS guidance here.
Does a no-logs VPN guarantee privacy if authorities request data?
No. No-logs claims reduce retention risk, but providers can still be compelled to assist. Prefer audited claims and simple architectures that minimize what could be captured. Treat VPNs as privacy tools, not anonymity guarantees.
When should I use Tor bridges instead of a VPN with obfuscation?
If your goal is anonymous browsing and your ISP blocks Tor, start with Tor bridges and pluggable transports. Use an obfuscated VPN when lawful and when you need broader app coverage or predictable egress regions.
Is VPN over Tor better than Tor over VPN, and what are the tradeoffs?
Neither is universally better. VPN over Tor can shield exits from seeing destinations but adds complexity and reliance on the VPN app. Tor over VPN can hide Tor usage from your ISP but shifts visibility to the VPN. Prefer bridges to layering when possible.
How do DNS and WebRTC leaks affect VPN and Tor users?
DNS leaks can reveal domains you visit to resolvers outside your tunnel. WebRTC can expose local or public IPs. Use clients that route DNS through the tunnel and review WebRTC settings based on your browser vendor guidance.
What’s the biggest mistake people make when relying on Tor or VPNs?
Assuming the tunnel makes them anonymous. Accounts, fingerprints, and devices often reveal more than IP addresses. Start with a clear threat model and maintain disciplined habits.
Key takeaways
- Tor with Tor Browser is stronger for browsing anonymity. VPNs are better for performance and region control.
- Your device and accounts often reveal more than your IP. Keep systems updated and identities separate.
- Treat VPNs as a trust transfer. Prefer audited providers with open, simple clients.
- Use Tor bridges or obfuscation to handle blocks where lawful. Layer only when you understand the risks.
- Test for leaks and review your setup regularly. Choose the simplest configuration that meets your goals.
- Stay legal and ethical. These tools are for privacy, safety, and authorized research, not for wrongdoing.