Last Updated on January 31, 2026 by DarkNet
Identity Anywhere by Avatier Password Management: A Detailed Overview of Pros and Cons
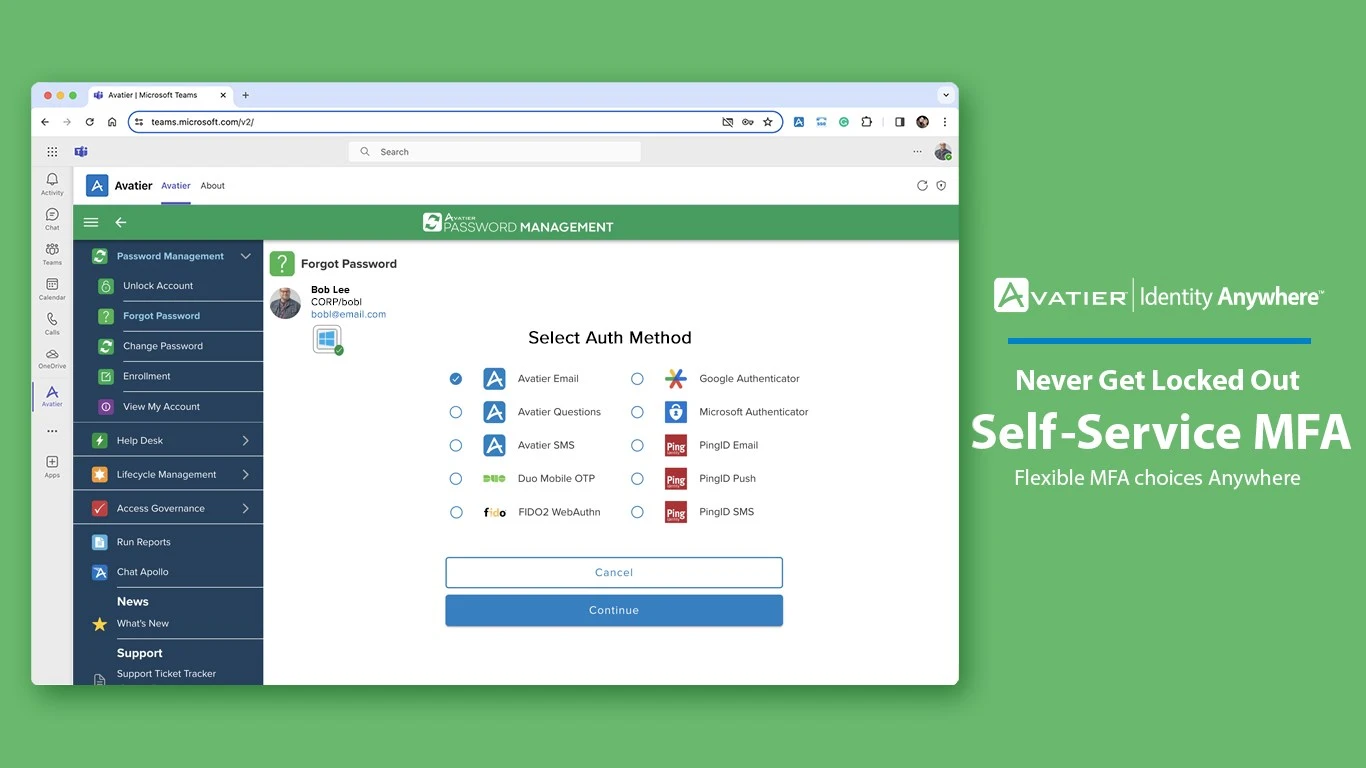
Avatier Identity Anywhere is an enterprise focused identity and password management platform. It is designed to support large organizations with centralized identity governance, password security, and self service access management across complex IT environments.
Below is a complete and objective overview of the main advantages and disadvantages of Identity Anywhere by Avatier.
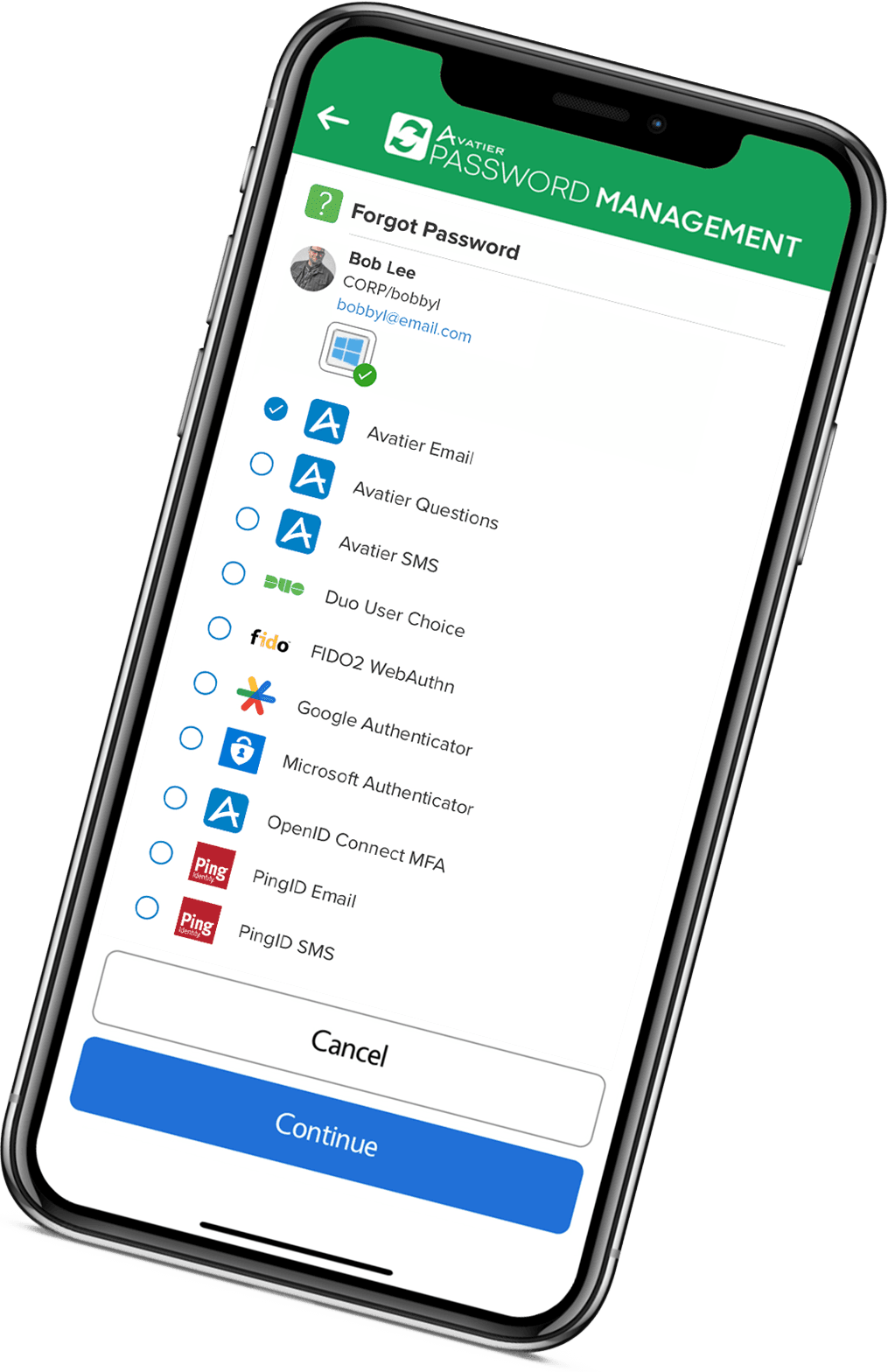
What Is Identity Anywhere
Identity Anywhere is a password and identity management solution built to:
- manage user identities and credentials centrally;
- enforce password policies across enterprise systems;
- provide secure self service password reset and access requests;
- support identity governance and compliance requirements.
The platform is primarily used in enterprise and government environments and integrates with on premises and cloud systems.
Core Features
- Enterprise password management and policy enforcement
- Self service password reset and account recovery
- Identity governance and access lifecycle management
- Role based access control
- Multi factor authentication support
- Audit logs and compliance reporting
- Integration with Active Directory and cloud identity providers
✅ Pros of Identity Anywhere
🔐 Strong Enterprise Security Model
- Centralized enforcement of password policies
- Secure handling of credentials across systems
- Support for multi factor authentication
- Designed to reduce identity related attack surfaces
This makes the platform suitable for high security environments.
🏢 Comprehensive Identity Management
- Combines password management with identity governance
- Manages access provisioning and deprovisioning
- Supports complex organizational structures
🔄 Self Service Password Reset
- Reduces help desk workload
- Allows users to securely reset passwords
- Improves productivity and user experience
📊 Compliance and Audit Readiness
- Detailed audit trails and reporting
- Supports regulatory and compliance requirements
- Clear visibility into identity and access activity
🧩 Broad Integration Capabilities
- Integrates with Active Directory, cloud apps, and enterprise systems
- Supports hybrid IT environments
- Works across on premises and cloud infrastructures
❌ Cons of Identity Anywhere
🧑💻 Not a Consumer Password Manager
- No personal password vault
- No browser based autofill for everyday websites
- Not intended for individual users
🎨 Complex Interface
- Interface prioritizes functionality over simplicity
- Steep learning curve for administrators
- Requires training and planning
⚙️ Deployment and Maintenance Complexity
- Implementation can be time consuming
- Requires dedicated IT and identity management expertise
- Ongoing maintenance and configuration needed
💰 Enterprise Level Pricing
- Pricing may be high for small organizations
- Overkill for simple password management needs
- Best suited for large scale deployments
Who Identity Anywhere Is Best For
Recommended if you:
- manage identities and passwords in a large organization;
- need centralized identity governance and compliance;
- want to reduce help desk load with self service resets;
- operate in regulated or high security environments.
Not ideal if you:
- want a personal or small team password manager;
- need browser autofill and consumer features;
- prefer a simple and lightweight solution.
Password Manager Comparison Table 2026
|
Product Name |
Encryption & Zero-Knowledge |
Platform Support |
Key Security Features |
Best For |
|---|---|---|---|---|
|
Yes, strong AES-256 + unique secret key |
All major OS & browsers |
Zero-knowledge, MFA, passkeys, secure sharing |
Premium security & usability |
|
|
Yes, AES-256, open-source |
All major OS & browsers |
Self-hosting option, open audit |
Open-source transparency & budget |
|
|
Yes, AES-256, zero-knowledge |
All major OS & browsers |
VPN (paid), breach monitoring |
Security insights + privacy tools |
|
|
Yes, zero-knowledge |
All major OS & browsers |
Password health, email masking |
Best overall value & simplicity |
|
|
Yes, AES-256 + PBKDF2 |
All major OS & browsers |
Self-destruct, secure sharing |
Enterprise & business focus |
|
|
Yes, encrypted vault |
All major OS & browsers |
Advanced form-filling |
Excellent form automation |
|
|
AES-256 local encryption |
All major OS & browsers |
Local-first vault, optional cloud sync |
Local control, no subscription |
|
|
Proton Pass |
Yes, AES-256 GCM, open-source |
All major OS & browsers |
End-to-end encryption, CLI access |
Privacy-focused, free tier strong |
|
LastPass |
Yes, encrypted vault (mixed fields) |
All major OS & browsers |
Cross-platform sync, 2FA |
Easy access, large user base |
|
Zoho Vault |
Yes, encrypted |
Web, apps |
Team sharing, access controls |
Business teams |
|
Yes, open-source |
Web & extensions |
Self-hosting, team roles |
Technical & DevOps teams |
|
|
Yes, E2E + hardware |
Web & mobile |
Hardware-first, FIDO2 |
Passwordless & simplicity |
|
|
Encrypted sync |
All major OS & browsers |
Integration with Dell ecosystem |
Enterprise users |
|
|
Encrypted |
Enterprise systems |
Active Directory integration |
Enterprise IT control |
|
|
Encrypted |
Enterprise systems |
User access & audit logs |
IT password governance |
|
|
Identity Anywhere (Avatier) |
Encrypted |
Enterprise systems |
Identity + SSO focus |
Large enterprise identity |
|
Bravura Pass |
Encrypted |
Enterprise |
Identity & privileged access |
Identity security suites |
|
Encrypted |
All major OS & browsers |
Multiple form filling |
General personal use |
|
|
Encrypted |
Unix-like systems |
Local system vault |
Linux-centric local vault |
|
|
KeePass (via forks like KeePassXC) |
Encrypted local vault |
All major OS |
Portable, local, plugin ecosystem |
Offline control & enthusiasts |
|
Encrypted |
Teams & enterprise |
Team collaboration |
Secure team vault |
Final Verdict
Identity Anywhere by Avatier is a powerful enterprise identity and password management platform built for organizations with complex security, compliance, and governance requirements. While it is not suitable for personal use and requires significant administrative effort, its strong identity controls, self service capabilities, and integration depth make it a solid choice for enterprises that need centralized and scalable identity security.